
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
There are a few different ways to route requests to a pod / service.
- Using an OpenShift route
- Using an ingress route
- Using a load balancer service
- Assign an external IP address to a service
An OpenShift route or an Ingress route will provide a URL such as http://my-route-my-project.apps.openshift.example.com which is used to route a request onto a service, which is then routed onto a pod, and then to the container in the pod, and finally to the application running in the container.
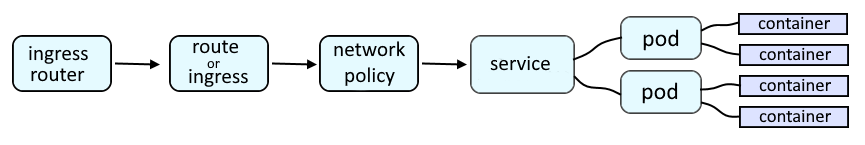
Like this.

The oc expose service command can be used to create an insecured route, whereas the oc create route command is used to create a secured route. The oc create route command can be used to create the following types of routes.
- edge = The connection is encrypted until it reaches the OpenShift Router. The connection is decrypted (TLS Termination) by the OpenShift Router.
- passthrough = The connection is encrypted as it moves through OpenShift. The connection is decrypted (TLS Termination) in the pod.
- reencrypt = The connection is encrypted as it reaches the OpenShift Router. The connection is decrypted (TLS Termination) by the OpenShift Router and then reencrypted with a different public certificate. The connection is then decrypted (TLS Termination) in the pod.
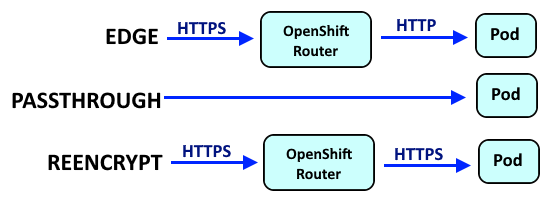
In this example, an edge route named my-route is created.
~]$ oc create route edge my-route --service my-service
route.route.openshift.io/my-route created
By default, an edge and reencrypt route will use the service CA certificate to secure the connection because the OpenShift Router will have the service CA private key needed to decrypt the connection (TLS Termination). In the openshift-ingress namespace, there should be a secret that contain the certificates used for TLS Termination on the OpenShift Router.
~]$ oc get secrets -n openshift-ingress
NAME TYPE DATA AGE
router-metrics-certs-default kubernetes.io/tls 2 508d
The following option can be used if you want to create an edge or reencrypt route with some other public certificate and private key. Since a passthrough route is decrypted by the pod, the service CA certificate is not used, which means that a passthrough route cannot be created with some other key pair. The public certificate must be in a PEM encoded file and must not be password protected.
oc create route edge my-route --service my-service --cert foo.pem --key foo.key --dest-ca-cert destca.pem --ca-cert ca.pem
The --insecure-policy option can be used to allow, deny, or redirect HTTP requests to HTTPS.
oc create route reencrypt my-route --service my-service --insecure-policy Redirect
If you have more than one type of ingress routers, such as "default" and "internal" and "external" in this example . . .
~]$ oc get pods --namespace openshift-ingress
NAME READY STATUS RESTARTS AGE
router-default-6f84fdff65-4zdmp 1/1 Running 0 557d
router-default-6f84fdff65-t7h22 1/1 Running 0 557d
router-default-6f84fdff65-z579b 1/1 Running 0 557d
router-internal-247fda1127-jmhv5 1/1 Running 0 342d
router-internal-247fda1127-sqqhc 1/1 Running 0 342d
router-internal-247fda1127-knlt2 1/1 Running 0 342d
router-external-f58b6de991-qng54 1/1 Running 0 340d
router-external-6f84fdff65-vcrn2 1/1 Running 0 340d
router-external-6f84fdff65-px6s8 1/1 Running 0 340d
You may need to label the route to get the route exposed on one of the ingress routers, such as the "default" or "internal" or "external" routers.
oc label route my-route route-type=default
The oc get routes command can then be used the list the routes. In this example, the URL to request the service is http://my-route-my-project.apps.openshift.example.com.
~]$ oc get routes
NAME HOST/PORT PATH SERVICES PORT TERMINATION WILDCARD
my-route my-route-my-project.apps.openshift.example.com my-service 8080-tcp edge None
Or the --hostname option can be used to give the route a specific URL.
oc create route edge my-route --service my-service --hostname a.apps.openshift.example.com
Often you will also want to specify the --port of the service/pod that the route should forward requests onto.
oc create route edge my-route --service my-service --hostname a.apps.openshift.example.com --port 8443
By default, the route will use the service CA certificate to secure the connection. In this scenario, the route will not list the public certificate and private key being used to secure the connection. On the other hand, if the route was created with a specified public certificate and private key, then this one liner can be used to display details for the public certificate.
~]$ oc get route my-route --output jsonpath={.spec.tls.certificate} | openssl x509 -noout -text
Certificate:
Data:
Serial Number:
9b:24:90:83:6b:e9:13:a7
Issuer: C=US, ST=California, L=Los Angeles, O=FreeKB, OU=IT, CN=example.com
Validity
Not Before: Sep 29 01:32:47 2022 GMT
Not After : Sep 29 01:32:47 2023 GMT
Subject: C=US, ST=California, L=Los Angeles, O=FreeKB, OU=IT, CN=example.com
The default router pod should be in the openshift-ingress project.
~]$ oc get pods --namespace openshift-ingress
NAME READY STATUS RESTARTS AGE
router-default-f6d44996c-sljgl 1/1 Running 2 (58m ago) 56d
The router pods run an haproxy (high availability proxy) load balancer, which can be seen with the oc exec command.
~]$ oc exec pod/router-default-76c5c89559-dclkw --namespace openshift-ingress -- cat /var/lib/haproxy/conf/haproxy.config | grep my-route
server pod:my-pod:my-service:8080-tcp:10.129.7.69:8080 10.129.7.69:8080 cookie 15b9071e86b87a2b4b6f976291de96cf weight 256 check inter 5000ms
If the application in the pod is a web based application, you should now be able to interact with the application using the route URL.
Or using curl.
~]# curl my-route-my-project.apps.openshift.example.com
Hello OpenShift!
Did you find this article helpful?
If so, consider buying me a coffee over at 