
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
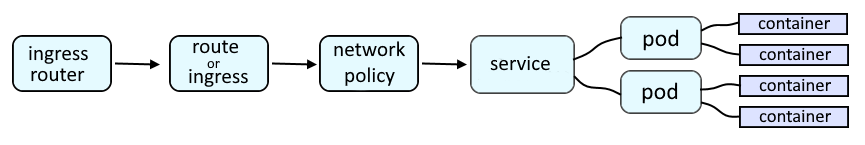
An OpenShift route or an Ingress route will provide a URL such as http://route001-project001.apps.openshift.example.com:8080 which is used to route a request onto a service, which is then routed onto a pod, and then to the container in the pod, and finally to the application running in the container.
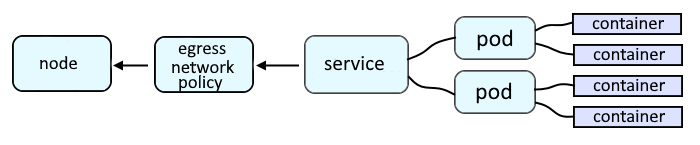
Egress provides a way for an application deployed on OpenShift to access an external URL, such as http://www.example.com.
The Ingress Controllers and Ingress Routers are responsible for allowing external requests access to routes/services/pods/apps.
The oc get ingresscontroller command can be used to list the Ingress Controllers which are in the openshift-ingress-operator namespace.
~]$ oc get ingresscontroller --namespace openshift-ingress-operator
NAME AGE
default 360d
external-router 356d
internal-router 356d
The oc get services command can be used to list the Ingress Routers which are in the openshift-ingress namespace.
~]$ oc get services --namespace openshift-ingress
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
router-internal-default ClusterIP 172.30.147.55 <none> 80/TCP,443/TCP,1936/TCP 423d
router-internal-external-router ClusterIP 172.30.173.34 <none> 80/TCP,443/TCP,1936/TCP 419d
router-internal-internal-router ClusterIP 172.30.209.168 <none> 80/TCP,443/TCP,1936/TCP 419d
router-nodeport-external-router NodePort 172.30.21.4 <none> 80:32080/TCP,443:32443/TCP 419d
router-nodeport-internal-router NodePort 172.30.185.219 <none> 80:31080/TCP,443:31443/TCP 419d
The oc describe ingresscontroller command can be used to display more information about an Ingress Controller.
~]$ oc describe ingresscontroller default --namespace openshift-ingress-operator
Name: default
Namespace: openshift-ingress-operator
Labels: <none>
Annotations: <none>
API Version: operator.openshift.io/v1
Kind: IngressController
Metadata:
Creation Timestamp: 2021-07-16T17:13:54Z
Finalizers:
ingresscontroller.operator.openshift.io/finalizer-ingresscontroller
Generation: 4
Managed Fields:
API Version: operator.openshift.io/v1
Fields Type: FieldsV1
fieldsV1:
f:metadata:
f:annotations:
.:
f:kubectl.kubernetes.io/last-applied-configuration:
f:spec:
f:replicas:
f:routeSelector:
.:
f:matchLabels:
.:
f:route-type:
Manager: kubectl-client-side-apply
Operation: Update
Time: 2021-07-20T18:21:18Z
API Version: operator.openshift.io/v1
Fields Type: FieldsV1
fieldsV1:
f:spec:
f:defaultCertificate:
.:
f:name:
f:nodePlacement:
.:
f:nodeSelector:
.:
f:matchLabels:
.:
f:default-router:
Manager: kubectl-patch
Operation: Update
Time: 2021-09-15T17:51:57Z
API Version: operator.openshift.io/v1
Fields Type: FieldsV1
fieldsV1:
f:metadata:
f:finalizers:
.:
v:"ingresscontroller.operator.openshift.io/finalizer-ingresscontroller":
f:spec:
f:status:
.:
f:availableReplicas:
f:conditions:
f:domain:
f:endpointPublishingStrategy:
.:
f:type:
f:observedGeneration:
f:selector:
f:tlsProfile:
.:
f:ciphers:
f:minTLSVersion:
Manager: ingress-operator
Operation: Update
Time: 2021-10-14T15:24:30Z
Resource Version: 411503452
UID: f1674657-2e23-444e-9839-83c0fd479448
Spec:
Default Certificate:
Name: apps-cert-2022
Node Placement:
Node Selector:
Match Labels:
Default - Router:
Replicas: 3
Route Selector:
Match Labels:
Route - Type: default
Status:
Available Replicas: 3
Conditions:
Last Transition Time: 2021-07-16T17:13:55Z
Reason: Valid
Status: True
Type: Admitted
Last Transition Time: 2022-06-22T14:14:34Z
Status: True
Type: PodsScheduled
Last Transition Time: 2022-06-22T14:08:50Z
Status: True
Type: Available
Last Transition Time: 2022-06-22T14:08:50Z
Message: The deployment has Available status condition set to True
Reason: DeploymentAvailable
Status: True
Type: DeploymentAvailable
Last Transition Time: 2022-06-22T14:08:50Z
Message: Minimum replicas requirement is met
Reason: DeploymentMinimumReplicasMet
Status: True
Type: DeploymentReplicasMinAvailable
Last Transition Time: 2022-06-22T14:15:04Z
Message: All replicas are available
Reason: DeploymentReplicasAvailable
Status: True
Type: DeploymentReplicasAllAvailable
Last Transition Time: 2021-07-16T17:13:55Z
Message: The configured endpoint publishing strategy does not include a managed load balancer
Reason: EndpointPublishingStrategyExcludesManagedLoadBalancer
Status: False
Type: LoadBalancerManaged
Last Transition Time: 2021-07-16T17:13:55Z
Message: No DNS zones are defined in the cluster dns config.
Reason: NoDNSZones
Status: False
Type: DNSManaged
Last Transition Time: 2021-10-05T13:56:44Z
Status: False
Type: Degraded
Domain: apps.openshift.example.com
Endpoint Publishing Strategy:
Type: HostNetwork
Observed Generation: 4
Selector: ingresscontroller.operator.openshift.io/deployment-ingresscontroller=default
Tls Profile:
Ciphers:
TLS_AES_128_GCM_SHA256
TLS_AES_256_GCM_SHA384
TLS_CHACHA20_POLY1305_SHA256
ECDHE-ECDSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-GCM-SHA256
ECDHE-ECDSA-AES256-GCM-SHA384
ECDHE-RSA-AES256-GCM-SHA384
ECDHE-ECDSA-CHACHA20-POLY1305
ECDHE-RSA-CHACHA20-POLY1305
DHE-RSA-AES128-GCM-SHA256
DHE-RSA-AES256-GCM-SHA384
Min TLS Version: VersionTLS12
Events: <none>
Did you find this article helpful?
If so, consider buying me a coffee over at 