
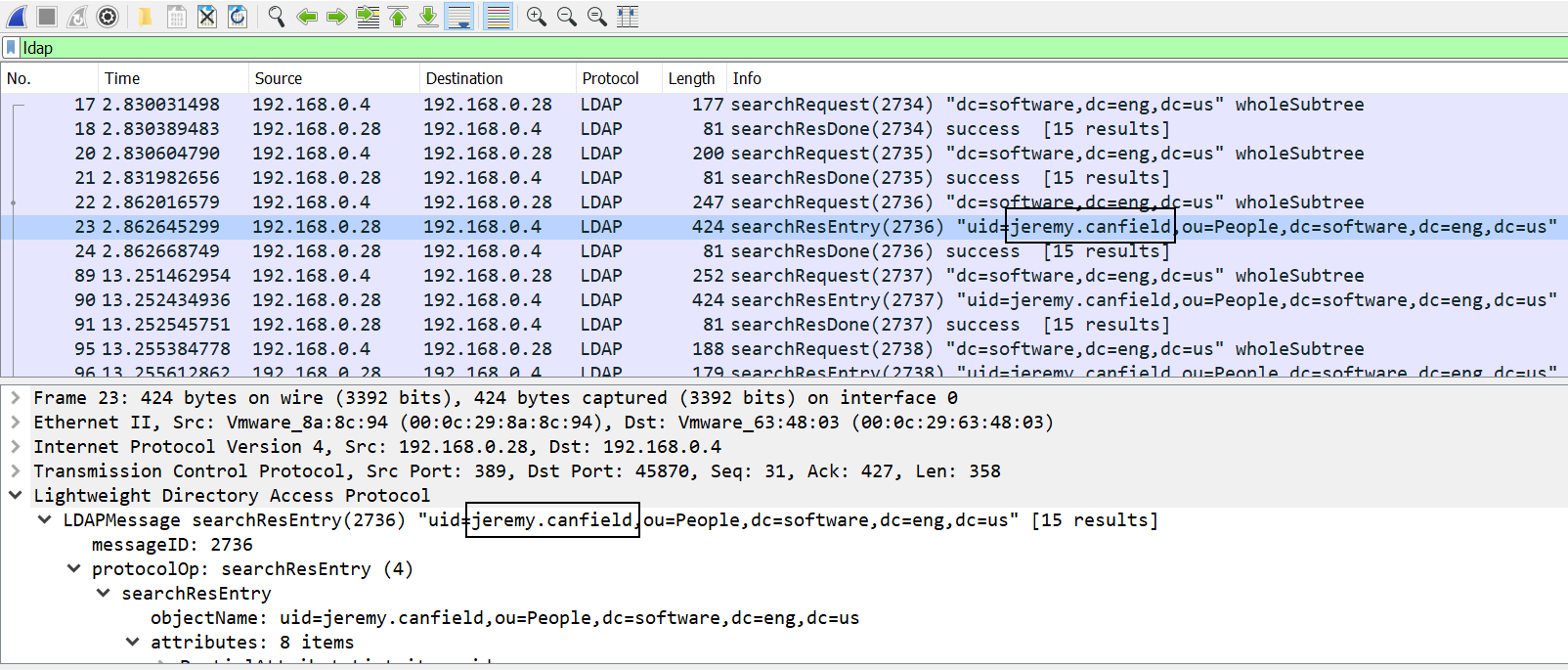
By default, OpenLDAP does not encrypt traffic. This produces a security risk, as sensitivie user information, such as user names can be captured. In this example, Wireshark captures unencrypted LDAP traffic, and my username is easily spotted.
OpenLDAP Server Setup
Create a public certificate and private key using OpenSSL. Ensure the CN of the certificate matches the hostname of your OpenLDAP server, such as ldap.example.com.
Copy the root certificate authority, public certificate, and private key into the /etc/openldap/certs directory.
~]# cp /etc/pki/tls/certs/rootCA.pem /etc/openldap/certs
~]# cp /etc/pki/tls/certs/example.crt /etc/openldap/certs
~]# cp /etc/pki/tls/private/example.key /etc/openldap/certs
Change the owner and group owner to ldap.
~]# chown ldap:ldap /etc/openldap/certs/rootCA.pem
~]# chown ldap:ldap /etc/openldap/certs/example.crt
~]# chown ldap:ldap /etc/openldap/certs/example.key
Create a flle named tls_modify.ldif.
~]# touch /etc/openldap/slapd.d/tls_modify.ldif
Add the following content to the file. After the TLS public certificate and private key has been added, to modify the public certificate and private key, replace "add" with "replace".
dn: cn=config
changetype: modify
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/openldap/certs/rootCA.pem
add: olcTLSCertificateFile
olcTLSCertificateFile: /etc/openldap/certs/example.crt
add: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/openldap/certs/example.key
Run the following command to add the public certificate and private key to your LDAP configuration.
~]# ldapmodify -H ldapi:// -Y EXTERNAL -f tls_modify.ldif
Add ldaps:/// to /etc/sysconfig/slapd.
SLAPD_URLS="ldapi:/// ldap:///"
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to restart slapd.
systemctl restart slapd
If your system is using init, use the service command to restart slapd.
service slapd restart
OpenLDAP Client Setup
Copy the rootCA.pem file from the OpenLDAP server to the /etc/ldap directory on the client.
~]# scp root@openldap:/etc/openldap/certs/rootCA.pem /etc/openldap/cacerts/
Enable LDAP authentication via TLS.
~]# authconfig --enableldaptls --update
Ensure the changes have been properly set.
~]# authconfig --test | grep -i ldap
nss_ldap is enabled
LDAP+TLS is enabled
LDAP server = "ldap.example.com"
LDAP base DN = "dc=example,dc=com"
Ensure LDAP port 389 is open in iptables or firewalld.
Use the ldapwhoami command with the -ZZ (force STARTTLS) option to make a TLS encrypted connection to the OpenLDAP server. If "anonymous" is displayed, the connection was successful.
~]# ldapwhoami -H ldap://ldap.example.com -x -ZZ
anonymous
Did you find this article helpful?
If so, consider buying me a coffee over at 