
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
A Security Context Constraint is used to control certain things, such as:
- Whether or not a pod can be run as root
- Whether or not a pod can access the host OpenShift system
- Whether or not a pod can access the host OpenShift network
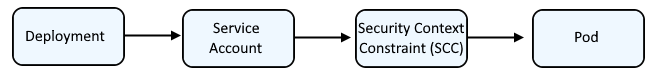
Typically, a Deployment is associated with a Service Account which has a certain Security Context Constraint (SCC) so that the pod runs with a certain Security Context Constraint (SCC).
Before deleting a Security Context Constraint, you will want to determine if the Security Context Constraint is being used by one or more Service Accounts. The oc describe clusterrolebinding command can be used. In this example the Security Context Constraint named "my-scc" is associated with my-service-account.
~]$ oc describe clusterrolebinding system:openshift:scc:my-scc
Name: system:openshift:scc:my-scc
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: system:openshift:scc:my-scc
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount my-service-account my-project
Since there is a service account associated with the Security Context Constraint, we next need to determine if there are any deployments or deployment configs using the Service Account. In this example, the "my-app" deployment is associated with the Service Account, thus also associated with the Security Context Constraint.
~]$ oc get deployment my-app --output yaml | oc adm policy scc-review -f -
RESOURCE SERVICE ACCOUNT ALLOWED BY
Deployment/v2-kube-state-metrics my-service-account my-scc
In this scenario, you could update the Deployment, remove the Service Account from the Deployment, which will also disassociated the Security Context Constraint from the Deployment. In this scenario, you could simply remove these directives from the deployment YAML.
serviceAccount: my-service-account
serviceAccountName: my-service-account
And then reissue this command to validate that the deployment is no longer associated with the Service Account and Security Context Constraint
~]$ oc get deployment my-app --output yaml | oc adm policy scc-review -f -
RESOURCE SERVICE ACCOUNT ALLOWED BY
Deployment/v2-kube-state-metrics my-service-account my-scc
Now you can use the oc adm policy remove-scc-from-user command to remove the Security Context Constraint from the Service Account.
~]$ oc adm policy remove-scc-from-user restricted -z my-service-account
clusterrole.rbac.authorization.k8s.io/system:openshift:scc:restricted removed: "my-service-account"
And now the the oc describe clusterrolebinding command should return "not found".
~]$ oc describe clusterrolebinding system:openshift:scc:my-scc
Error from server (NotFound): clusterrolebindings.rbac.authorization.k8s.io "system:openshift:scc:my-scc" not found
Last but not least, now you can delete the Service Account.
~]$ oc delete serviceaccount my-service-account
serviceaccount "my-service-account" deleted
Did you find this article helpful?
If so, consider buying me a coffee over at 