
Let's say you've deployed an application to ArgoCD but the app remains OutOfSync.
~]$ argocd app list
NAME CLUSTER NAMESPACE PROJECT STATUS HEALTH SYNCPOLICY CONDITIONS REPO PATH TARGET
openshift-gitops/demo https://kubernetes.default.svc my_project default OutOfSync Missing Manual <none> https://github.com/my_project/my_repo.git python
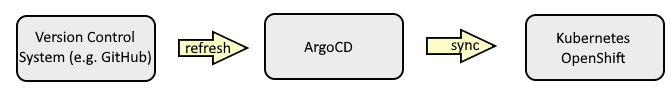
- Sync an app (Push the YAML manifests in ArgoCD to Kubernetes or OpenShift)
- Refresh a repo (The YAML manifest in ArgoCD will be compared to the YAML in the version control system (such as GitHub) and if any differences are detected the YAML manifest in ArgoCD will be updated to match the YAML in the version control system (such as GitHub))
- Hard Refresh a repo (YAML manifests in ArgoCD are cached - A hard refresh invalidates the cache which forces the YAML manifests in ArgoCD to match the YAML in the version control system (such as GitHub))
Almost always, this is because the openshift-gitops-argocd-application-controller permission Service Account does not have permission to create an application in a certain namespace. Notice in this example that the application was deployed to my_project. The oc adm policy who-can command can be used to determine if the openshift-gitops-argocd-application-controller permission Service Account has permission to create app. In this example, openshift-gitops-argocd-application-controller permission does not have permission to create app in my_project.
~]$ oc adm policy who-can create app --namespace my_project
Namespace: my_project
Verb: create
Resource: applications.argoproj.io
Users: system:admin
system:serviceaccount:openshift-gitops-operator:openshift-gitops-operator-controller-manager
Groups: Openshift_Admin
openshift_admins
openshift_operators
system:cluster-admins
system:masters
The oc adm policy add-role-to-user command can be used to give the openshift-gitops-argocd-application-controller permission Service Account the admin permission in my_project.
oc adm policy add-role-to-user admin system:serviceaccount:openshift-gitops:openshift-gitops-argocd-application-controller --namespace my_project
Did you find this article helpful?
If so, consider buying me a coffee over at 