
The easist way to install the latest stable version of OpenSSL is to use your systems package manage. On a Debian distribution, apt-get can be used to install OpenSSL.
apt-get install openssl
On a Red Hat distribution (CentOS, Fedora, Red Hat), dnf or yum can be used to install OpenSSL.
dnf install openssl
Private key
A public certificate and it's corresponding private key can be used to encrypt packets being transmitted between hosts. One of the most popular uses of a public certificate and it's corresponding private key is to encrypt the resources being transmitted to clients from a web server, so that HTTPS can be used. The first step is to create the private key. In this example, the private key is placed on the web server. As the name implies, a private key is private, and should never be made public.
Refer to Create private key using OpenSSL on Linux for the steps on how to create the private key.
Certificate Signing Request (CSR)
The certificate signing request (CSR) file is used to add personal information to the public certificate, such as your company name and location. The CSR also contains a reference to the private key.

There are two ways to go about creating the CSR file. You can either enter the information into an interactive prompt, or you can create the CSR file from a config file. Refer to Create CSR (certificate signing request) using OpenSSL on Linux for the steps on how to create the CSR.
Public certificate (aka X.509)
The public certificate is what is provided to the clients. There is a mathmatical relationship between the public certificate and private key. Both are needed in order for encryption to work.
Refer to Create an RSA public certificate using OpenSSL on Linux for the steps on how to create an RSA public certificate.

Using the public / private key pair
You can now use the public / private key pair. In this example, the private key and public certificate are placed on the web server. The CSR file is not used by the web server.
Internet facing production applications should use a certificate from a trusted CA, such as verisign.com. For non-production applications, a self-signed certificate can be used. Applications, such as a web browser, will complain when a self-signed certificate is used.
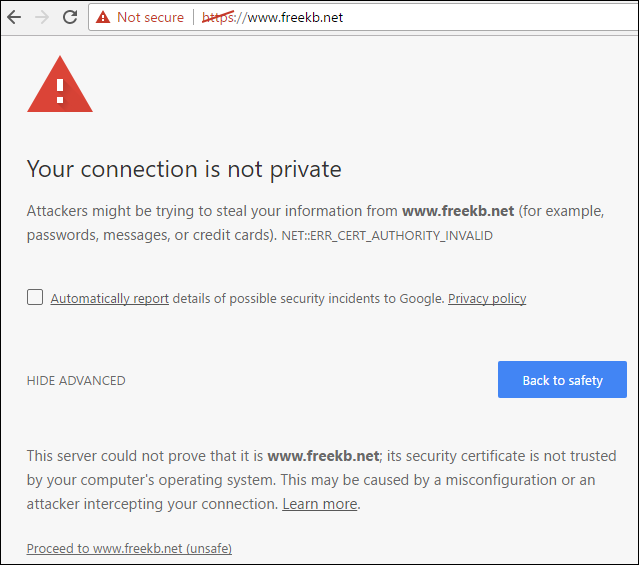
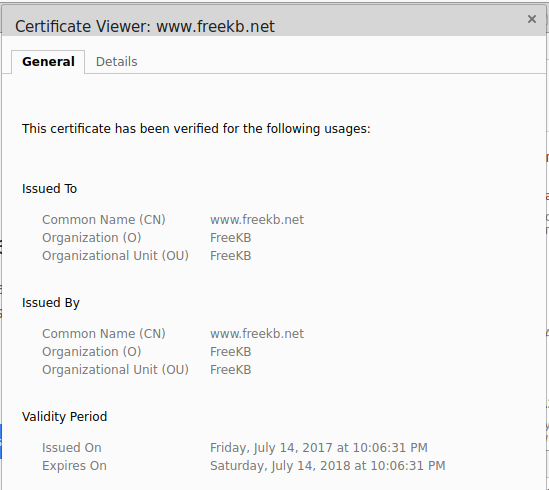
When the client navigates to an HTTPS page, the client will request the public certificate from the web server, and then the public certificate will reside on the clients browser for a period of time. The certificate can be viewed by the client.
Did you find this article helpful?
If so, consider buying me a coffee over at 