
First and foremost, before you even starting working through configuring Tomcat to use SSL, you should ask yourself it it makes sense to configure Tomcat to use SSL. For example, let's say Tomcat is going to sit behind a web server. In this situation, if the web server is configured to use SSL, it may not make sense to configure Tomcat to use SSL. And you don't just configure SSL for fun. SSL adds latency and increased burden on CPU and memory, as well as actual money as you need to pay for a trusted certificate. Read on if you still want to configure Tomcat to use SSL.
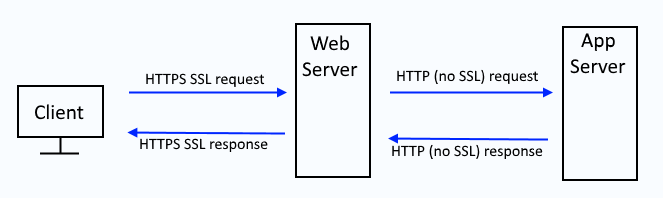
It's important to recongize that there will be both inbound and outbound requests. Typically, an inbound request is when a remote system makes a request for an app deployed to Tomcat. Typically, and outbound request is when an app deployed to Tomcat needs to go out, such as when making a query to a remote SQL database. This article only deals with securing inbound requests. Refer to this article to secure outbound requests.
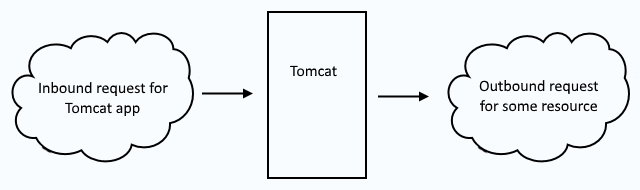
Inbound requests use a keystore to secure the requests. Outbound requests use a truststore to secure the request. So, when you see keystore, think "inbound" and when you see truststore think "outbound".
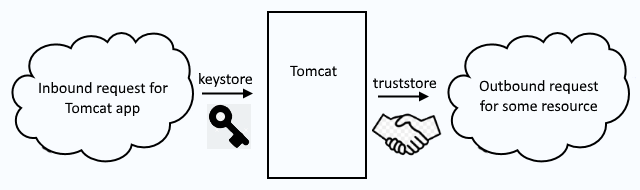
First you will create a keystore that contains the public/private keypair used for SSL for the inbound connections to Tomcat, and then you will configure Tomcat. If you have not yet created a keystore, refer to this article.
By default, your $CATALINA_HOME/conf/server.xml file should have the SSL configuration commented out with the <!-- and --> tags. Remove the <!-- and --> tags.
<!--
<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true" >
<SSLHostConfig>
<Certificate certificateKeystoreFile="conf/localhost-rsa.jks" type="RSA" />
</SSLHostConfig>
</Connector>
-->
OpenSSL can be used to see if you are able to make a connection on port 8443.
~]$ openssl s_client -connect tomcat.exmaple.com:8443
CONNECTED(00000003)
Verify return code: 0 (ok)
Revise the Connector to have the following. Notice keystoreFile is ssl/my_keystore.p12.
The keystoreFile can either be the relative or absolute path to the keystore file. In this example, the keystore named my_keystore.p12 would have to be located at $CATALINA_HOME/ssl/my_keystore.p12.
The keystore will contain the public certificates and private key needed for SSL. If you don't have a keystore, check out my article on how to create a keystore using the Java keytool command.
<Connector
port="8443"
protocol="HTTP/1.1"
SSLEnabled="true"
maxThreads="150"
scheme="https"
secure="true"
clientAuth="false"
sslProtocol="TLS"
keystoreFile="ssl/my_keystore.p12"
keystorePass="itsasecret"
keyAlias="tomcat.example.com"
ciphers="TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,
TLS_ECDHE_RSA_WITH_RC4_128_SHA,
TLS_RSA_WITH_AES_128_CBC_SHA256,
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA256,
TLS_RSA_WITH_AES_256_CBC_SHA,
SSL_RSA_WITH_RC4_128_SHA"
/>
Restart Tomcat.
$CATALINA_HOME/bin/shutdown.sh
$CATALINA_HOME/bin/startup.sh
You should now be able to navigate to https://<hostname or IP address of your Tomcat system>:8443.
Did you find this article helpful?
If so, consider buying me a coffee over at 