
First and foremost, it's important to recongize that an application running on Tomcat will have both inbound and outbound requests. Typically, an inbound request is when a remote system makes a request for some resource from an app deployed to Tomcat. Typically, and outbound request is when an app deployed to Tomcat needs to go out, such as when making a query to a remote SQL database. This article only deals with securing outbound requests. Refer to this article to secure inbound requests.
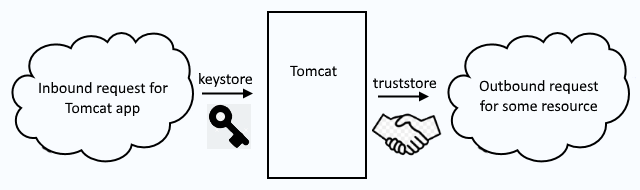
Inbound requests use a keystore to secure the requests. Outbound requests use a truststore to trust the connection between the app running on Tomcat and the remote system. So, when you see keystore, think "inbound" and when you see truststore think "outbound".
As an example, let's say your app running on Tomcat needs to download the foo.txt file from www.example.com over a secured HTTPS connection. If the Tomcat app is NOT configured to trust https://www.example.com, the Tomat catalina.out logs should contain something like this.
javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
In this scenario, you will first need to create a trust store file, such as trust.jks or cacerts.p12 (it can be named anything you want), which can be done using the Java keytool command.
keytool -keystore trust.p12 -storetype pkcs12 -storepass itsasecret -genkey -alias placeholder -keyalg RSA -keysize 2048
Then remove the private key that was created in trust.p12.
keytool -keystore trust.p12 -storetype pkcs12 -storepass itsasecret -delete -alias placeholder
You will then obtain the public certificate for www.example.com and then import the certificate into the trust store.
keytool -keystore trust.p12 -storetype pkcs12 -storepass itsasecret -import -alias www.example.com -file www.example.com.cer
You will then need to configure your Tomcat application server to use the trust store file. This is often done by adding the following key value pairs to the JAVA_OPTS variable in ${tomcat_install_root}/bin/setenv.sh.
TRUSTSTORE="-Djavax.net.ssl.trustStore=/path/to/trust.p12"
TRUSTSTORE_PASSWORD="-Djavax.net.ssl.trustStorePassword=itsasecret"
JAVA_OPTS="$TRUSTSTORE $TRUSTSTORE_PASSWORD"
You may want to also include the following debug parameter.
JAVA_OPTS="$TRUSTSTORE $TRUSTSTORE_PASSWORD -Djavax.net.debug=ssl"
And then restart your Tomcat application server for this change to take effect.
$CATALINA_HOME/bin/shutdown.sh
$CATALINA_HOME/bin/startup.sh
Now, your Tomcat app should be able to download the foo.txt file from www.example.com over HTTPS.
Did you find this article helpful?
If so, consider buying me a coffee over at 