
Lightweight Third Party Authentication (LTPA) is a single-sign on (SSO) protocol. By default, WebSphere uses LTPA for SSO. As an example, when you sign into the WebSphere admin console, an LTPA token will be issued. The LTPA token will remain active for a period of time (120 minutes by default). For the lifespan of the LTPA token, when you navigate to any WebSphere admin console in the same DNS domain that contains the LTPA key, you will not need to authenticate again by providing a username and password. Instead, you will be automatically authenticated into the admin console via the LTPA token.
Configure WebSphere to use LTPA
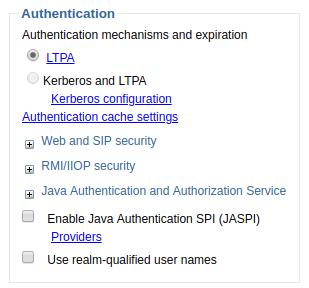
By default, at Security > Global Security, WebSphere is configured to use LTPA. Selecting LTPA will let you configure LTPA.
Likewise, the HPEL or SystemOut.log will identify the authentication mechanism being used.
JSAS0003I: Authentication mechanism: LTPA
Get LTPA token
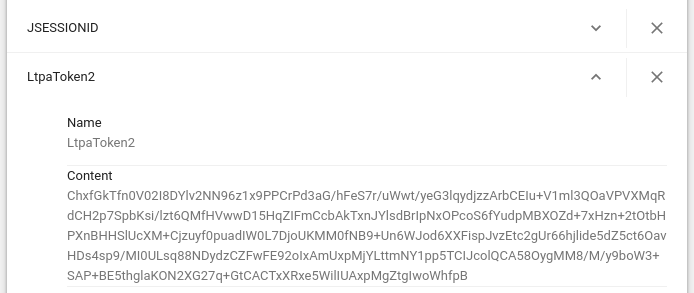
By default, log level is *=info. At this log level, the LTPA token will not be recorded in SystemOut.log or HPEL log. Updating the log level to fine, finer, or finest will make it so that the LTPA token is recorded in the log, like this.
LtpaToken2=ChxfGkTfn0V02I8DYlv2NN96z1x9PPCrPd3aG/hFeS7r/uWwt/yeG3lqydjzzArbCEIu+V1ml3QOaVPVXMqRdCH2p7SpbKsi/lzt6QMfHVwwD15HqZIFmCcbAkTxnJYlsdBrIpNxOPcoS6fYudpMBXOZd+7xHzn+2tOtbHPXnBHHSlUcXM+Cjzuyf0puadIW0L7DjoUKMM0fNB9+Un6WJod6XXFispJvzEtc2gUr66hjlide5dZ5ct6OavHDs4sp9/MI0ULsq88NDydzCZFwFE92oIxAmUxpMjYLttmNY1pp5TCIJcolQCA58OygMM8/M/y9boW3+SAP+BE5thglaKON2XG27q+GtCACTxXRxe5WilIUAxpMgZtgIwoWhfpB
Or, you can get the LTPA token by viewing the web browser cookies.
Destroying LTPA token
Following are the three most common events that will cause the LTPA token to be destroyed.
- Clicking Logout in the WebSphere admin console
- Closing the web browser (all browser tabs)
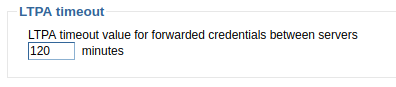
- The LTPA token timeout period is reached. By default, the LTPA timeout is 120 minutes.
Closing only the browser tab for the WebSphere admin console but leaving the other browser tabs open will not destroy the LTPA token because this action does not remove the LtpaToken2 cookie from the browsers cache.
Likewise, the /opt/WebSphere/AppServer/profiles/your_profile/config/cells/your_cell/security.xml file should contain a line like this.
<authMechanisms
xmi:type="security:LTPA"
xmi:id="LTPA_1"
OID="oid:1.3.18.0.2.30.2"
authContextImplClass="com.ibm.ISecurityLocalObjectTokenBaseImpl.WSSecurityContextLTPAImpl"
authConfig="system.LTPA"
simpleAuthConfig="system.LTPA"
authValidationConfig="system.LTPA"
timeout="120"
keySetGroup="KeySetGroup_1">
Sharing LTPA between Websphere servers
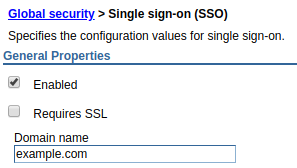
If you have two or more WebSphere servers in the same DNS domain, and can create an LTPA key on one of your WebSphere servers and then use the LTPA key to be automatically authenticated to the other WebSphere servers. You will also want to configure each WebSphere server with the same domain name.
Encryption
By default, LTPA tokens are encrypted using a public certificate and private key. In this example, the ltpa.jceks file is the keystore that contains the public certificate and private key used to encrypt LTPA tokens.
Did you find this article helpful?
If so, consider buying me a coffee over at 