
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
Role Bindings are a way to map subjects (user, group, service account) to a Role or Cluster Role, so that the subjects have permission to perform certain actions (e.g. create, delete) on certain resources (e.g. deployments, secrets). In other words, Role Bindings are a way to apply Role Based Access Control (RBAC). Here is an illustration of how subjects (user, group, service account) get mapped to permissions. There are a number of different ways to design this, typically based on your organizations needs.
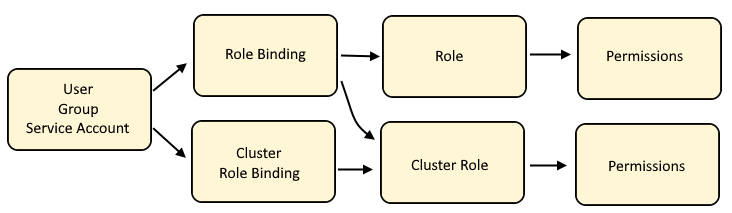
Cluster Role Binding maps a user, group or service account to a Cluster Role which will have policies that allow certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
Role Bindings maps a user, group or service account to a Role or to a Cluster Role which will have policies that allow certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
Cluster Role is often used by a number of different users, groups and service accounts in various projects, thus a Cluster Role contains the default actions (such as list, get, watch) on certain resources (such as deployments, pods) that users, groups, or service accounts are allowed to do across namespaces.
Role if isolated to a user, group or service account in a specific project, as a way of granting specific actions (such as create and delete and update) on certain resources (such as services and routes).
The oc describe role and oc describe clusterrole commands can be used to list the permissions of what is allowed with a Role or Cluster Role.
~]$ oc describe ClusterRole admin
Name: admin
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
clusterlogforwarders.logging.openshift.io [] [] [* create update patch delete get list watch]
clusterloggings.logging.openshift.io [] [] [* create update patch delete get list watch]
serviceaccounts [] [] [create delete deletecollection get list patch update watch impersonate]
buildconfigs/webhooks [] [] [create delete deletecollection get list patch update watch]
buildconfigs [] [] [create delete deletecollection get list patch update watch]
buildlogs [] [] [create delete deletecollection get list patch update watch]
Role Bindings and Security Context Constraint are similar in that they both are access control mechanisms.
- Role Bindings are used to allow users, groups and service accounts certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
- Security Context Constraints are used to control what pods are allowed to do
Roles and Cluster Roles
Before creating a Role Binding or Cluster Role Binding that maps to a Cluster Role, the oc get clusterrole command can be used to determine if the Cluster Role exists.
~]$ oc get clusterrole cluster-admin
NAME CREATED AT
cluster-admin 2023-07-07T15:30:54
Or in the OpenShift console at User Management > Roles, you can search for the Cluster Role.
If the Cluster Role does not exist, you can create the Cluster Role. Check out my article FreeKB - OpenShift - Create Roles.
oc create clusetrrole my-cluster-role --verb get --verb list --verb watch --resource pods
Similarly, before creating a Role Binding that maps to a Role (not a Cluster Role), the oc get role command can be used to determine if the Role exists.
~]$ oc get role my-role --namespace my-project
NAME CREATED AT
my-role 2025-06-18T01:23:03Z
Or in the OpenShift console at User Management > Roles, you can search for the Role.
If the Role does not exist, you can create the Role. Check out my article FreeKB - OpenShift - Create Roles.
oc create role my-role --verb get --verb list --verb watch --resource pods --namespace my-project
Determine if a User, Group or Service Account has permission to perform an action on a resource
Before creating a Role Binding or Cluster Role Binding, you will probably want to first determine if a User, Group or Service Account has permission to perform an action on a resource
Create Role Binding
Here is how you can create a Role Binding that is associated with a Cluster Role and not associated with any subjects (users, groups, service accounts). Since Role Bindings are not at the cluster level, the role binding must be created in a namespace. In this example, the Role Binding is created in namespace my-project.
It is noteworthy that you cannot create a Role Binding in the OpenShift console because you must select a subject (user, group, or service account) when creating the Role Binding in the OpenShift console.
oc create rolebinding my-role-binding --clusterrole cluster-admin --namespace my-project
The YAML of the Role Binding should return something like this.
~]$ oc get rolebinding my-role-binding --namespace my-project --output yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: "2025-06-17T01:24:06Z"
name: my-role-binding
namespace: my-project
resourceVersion: "552229779"
uid: 264e091c-80ae-4f57-b58f-f980a8a7b24a
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
Here is how you can create a Role Binding that is associated with a Role (not a Cluster Role) and not associated with any subjects (users, groups, service accounts). This is nearly identical to the prior command expect that the Role Binding is associated with a Role instead of a Cluster Role.
oc create rolebinding my-role-binding --role my-role --namespace my-project
The YAML of the Role Binding should return something like this.
~]$ oc get rolebinding my-role-binding --namespace my-project --output yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: "2025-06-17T01:35:00Z"
name: my-role-binding
namespace: my-project
resourceVersion: "552236367"
uid: ce69cf68-0a6d-4d53-9aa9-33a84722ee45
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: my-role
The --user option can be used to create a Role Binding that maps one or more users to the Role Binding, effectively granting the users the Role or Cluster Role associated with the Role Binding.
Remember to use the --role option if you want the Role Binding to reference a Role (not a Cluster Role).
oc create rolebinding my-role-binding --role my-role --user john.doe --namespace my-project
Or the following command can be used. In this example, the Role Binding will reference a Role (not a Cluster Role).
oc adm policy add-role-to-user my-role john.doe --rolebinding-name my-role-binding --role-namespace my-project --namespace my-project
Or use the --clusterrole option if you want the Role Binding to reference a Cluster Role.
oc create rolebinding my-role-binding --clusterrole cluster-admin --user john.doe --namespace my-project
Or the following command can be used. In this example, the Role Binding will reference a Cluster Role.
oc adm policy add-role-to-user cluster-admin john.doe --rolebinding-name my-role-binding --namespace my-project
Or in the OpenShift console at User Management > RoleBindings > Create RoleBinding
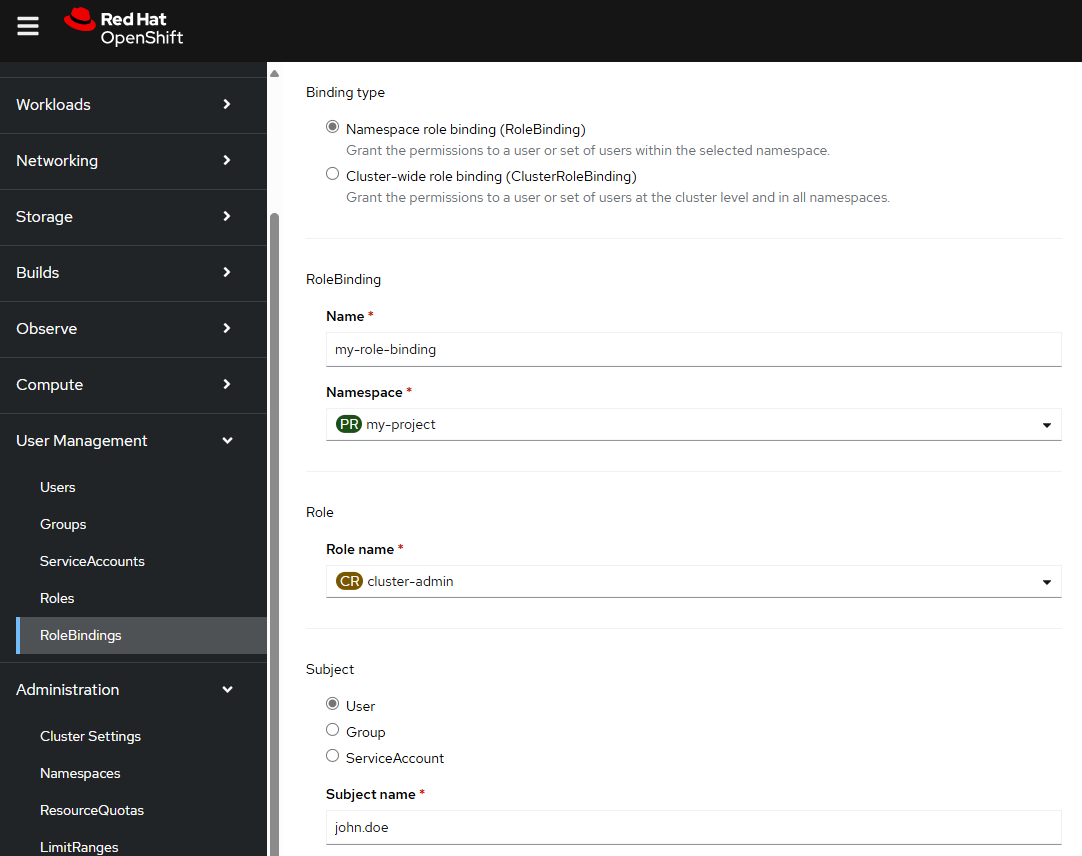
The YAML of the Role Binding should return something like this.
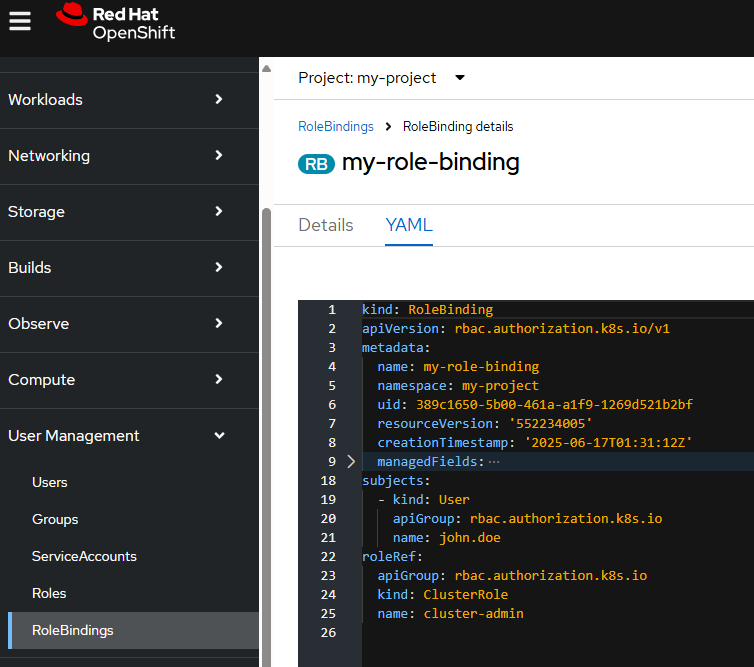
~]$ oc get rolebinding my-role-binding --output yaml --namespace my-project
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: "2025-06-17T01:31:12Z"
name: my-role-binding
namespace: my-project
resourceVersion: "552234005"
uid: 389c1650-5b00-461a-a1f9-1269d521b2bf
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: john.doe
Or in the OpenShift console at User Management > RoleBindings > your role binding > YAML tab
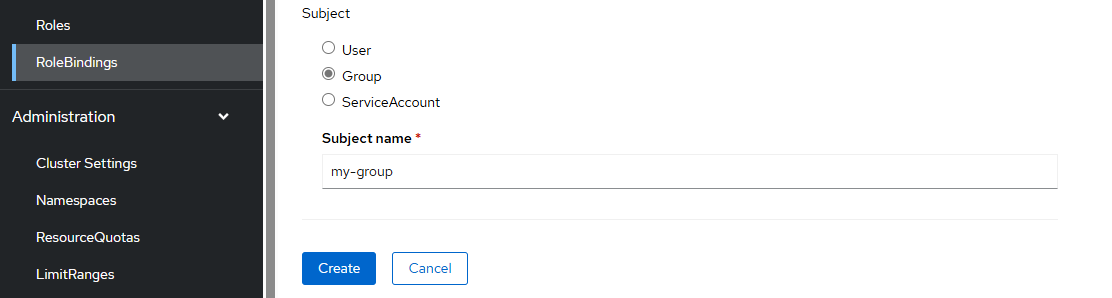
The --group option can be used to create a Role Binding that maps one or more groups to the Role Binding, effectively granting the users in the group the Role or Cluster Role associated with the Role Binding.
Remember to use the --role option if you want the Role Binding to reference a Role (not a Cluster Role).
oc create rolebinding my-role-binding --role my-role --group my-group --namespace my-project
Or use the --clusterrole option if you want the Role Binding to reference a Cluster Role.
oc create rolebinding my-role-binding --clusterrole cluster-admin --group my-group --namespace my-project
Or in the OpenShift console at User Management > RoleBindings > Create RoleBinding.
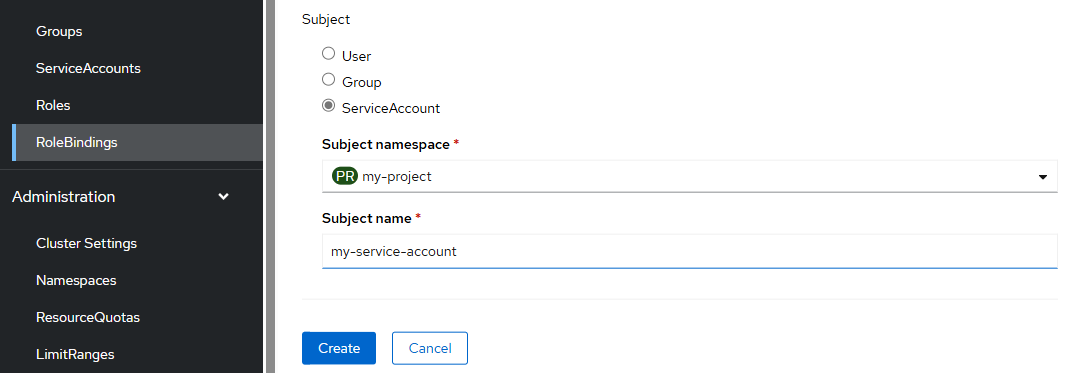
The --serviceaccount option can be used to create a Role Binding that maps one or more service accounts to the Role Binding, effectively granting the service accounts the Role or Cluster Role associated with the Role Binding.
Remember to use the --role option if you want the Role Binding to reference a Role (not a Cluster Role).
oc create rolebinding my-role-binding --role my-role --serviceaccount my-project:my-service-account --namespace my-project
Or use the --clusterrole option if you want the Role Binding to reference a Cluster Role.
oc create rolebinding my-role-binding --clusterrole cluster-admin --serviceaccount my-project:my-service-account --namespace my-project
Or in the OpenShift console at User Management > RoleBindings > Create RoleBinding.
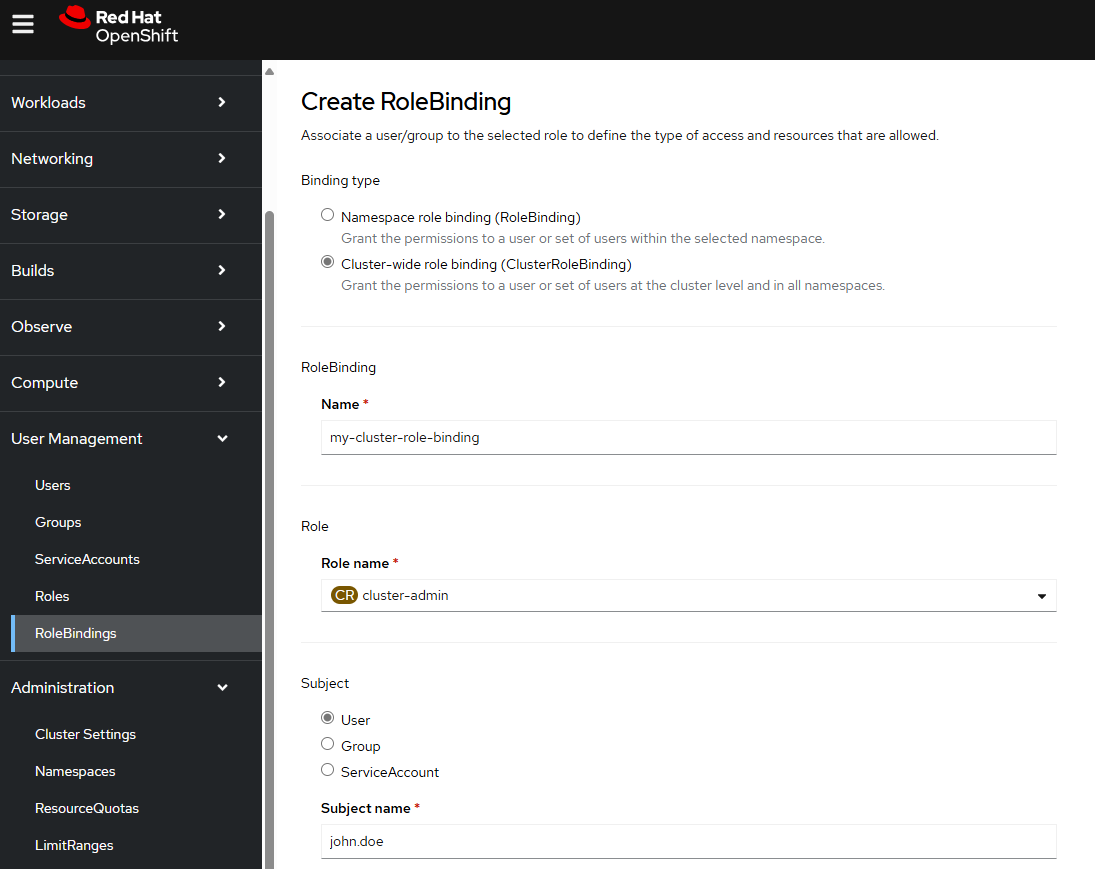
Create Cluster Role Binding
Here is how you can create a Cluster Role Binding that is associated with a Cluster Role and not associated with any subjects (users, groups, service accounts).
It is noteworthy that you cannot create a Cluster Role Binding in the OpenShift console that is not associated with a subject (user, group, service account) because when creating the Cluster Role Binding in the console, you must select a subject (user, group, service account).
oc create clusterrolebinding my-cluster-role-binding --clusterrole cluster-admin
The YAML of the Cluster Role Binding should return something like this.
~]$ oc get clusterrolebinding my-cluster-role-binding --output yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: "2025-06-17T01:09:41Z"
name: my-cluster-role-binding
resourceVersion: "552221142"
uid: 7c418eae-54d8-4268-a843-da60e0023efb
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
The --user option can be used to create a Cluster Role Binding that maps one or more users to the Cluster Role Binding, effectively granting the users the Cluster Role associated with the Cluster Role Binding.
oc create clusterrolebinding my-cluster-role-binding --clusterrole cluster-admin --user john.doe
Or in the OpenShift console at User Management > RoleBindings > Create RoleBinding.
The YAML of the Cluster Role Binding should return something like this.
~]$ oc get clusterrolebinding my-cluster-role-binding --output yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: "2025-06-17T01:10:16Z"
name: my-cluster-role-binding
resourceVersion: "552221453"
uid: da4d2969-a7e7-423a-91b4-64cd274ea7b9
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: john.doe
Or in the OpenShift console at User Management > RoleBindings > your role binding > YAML tab.
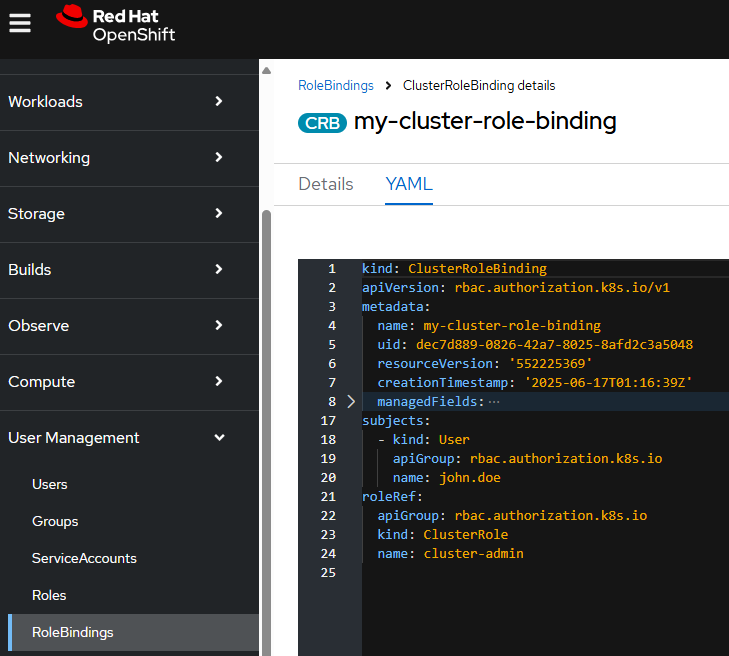
The --group option can be used to create a Cluster Role Binding that maps one or more groups to the Cluster Role Binding, effectively granting the users in the group the Cluster Role associated with the Cluster Role Binding.
oc create clusterrolebinding my-cluster-role-binding --clusterrole cluster-admin --group my-group
Or in the OpenShift console at User Management > RoleBindings > Create RoleBinding.

The --serviceaccount option can be used to create a Cluster Role Binding that maps one or more service accounts to the Cluster Role Binding, effectively granting the service accounts the Cluster Role associated with the Cluster Role Binding.
oc create clusterrolebinding my-cluster-role-binding --clusterrole cluster-admin --serviceaccount my-project:my-service-account
Or in the OpenShift console at User Management > RoleBindings > Create RoleBinding.

Add Role Binding to User / Group / Service Account
The oc adm policy add-role-to-user command can be used to add a role binding to a user.
~]# oc adm policy add-role-to-user my-basic-users john.doe
rolebinding.rbac.authorization.k8s.io/my-basic-users added: "john.doe"
Or a group.
~]$ oc adm policy add-role-to-group my-basic-users my_group
rolebinding.rbac.authorization.k8s.io/my-basic-users added: "my_group"
Or to a service account.
~]# oc adm policy add-role-to-user my-basic-users -z my-service-account
rolebinding.rbac.authorization.k8s.io/my-basic-users added: "my-service-account"
Remove Role Binding from a User / Group / Service Account
The oc adm policy remove-role-from-user command can be used to remove a role binding from a user.
~]# oc adm policy remove-role-from-user my-basic-users john.doe
rolebinding.rbac.authorization.k8s.io/my-basic-users removed: "john.doe"
Or from a service account.
~]# oc adm policy remove-role-from-user my-basic-users -z my-service-account
rolebinding.rbac.authorization.k8s.io/my-basic-users removed: "my-service-account"
The oc adm policy remove-role-from-group command can be used to remove a role from a group.
~]$ oc adm policy remove-role-from-group my-basic-users my_group
rolebinding.rbac.authorization.k8s.io/my-basic-users removed: "my_group"
Did you find this article helpful?
If so, consider buying me a coffee over at 