
Let's say something like this is being returned when attempting to do something in a project in OpenShift. For example, this could occur when issuing an oc command, such as oc get pods. In this example, john.doe does not have permission to issue the oc get pods command.
~]$ oc get pods
Error from server (Forbidden): pods is forbidden: User "john.doe" cannot list resource "pods" in API group "" in the namespace "default"
Or like this, when using the OpenShift REST API to submit a request.
forbidden: User \"system:anonymous\" cannot list resource \"rolebindings\" in API group \"rbac.authorization.k8s.io\" at the cluster scope
Here is an illustration of how a user, group or service account get mapped to permissions. There are a number of different ways to design this, typically based on your organizations needs.
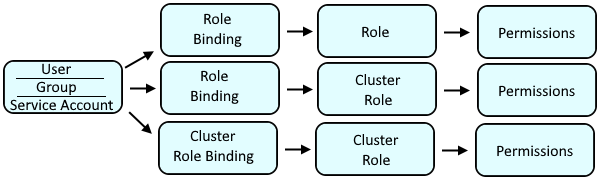
Cluster Role Binding maps a user, group or service account to a Cluster Role which will have policies that allow certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
Role Bindings maps a user, group or service account to a Role or to a Cluster Role which will have policies that allow certain actions (such as create or delete or list) on certain resources (such as deployments, pods)
Cluster Role is often used by a number of different users, groups and service accounts in various projects, thus a Cluster Role contains the default actions (such as list, get, watch) on certain resources (such as deployments, pods) that users, groups, or service accounts are allowed to do across namespaces.
Role if isolated to a user, group or service account in a specific project, as a way of granting specific actions (such as create and delete and update) on certain resources (such as services and routes).
To resolve this, you'll probably need to use the oc logout command and then use the oc login command to log in as a user that has the admin or cluster-admin role.
Determine if the user or group is mapped to a role binding
The oc list rolebindings command can be used to list the Role Bindings that have been created in a specific project.
~]$ oc get rolebinding --namespace my-project
NAME ROLE AGE
my-admins ClusterRole/admin 157s
my-basic-users ClusterRole/basic-user 106s
my-view-only ClusterRole/view 205s
The oc list clusterrolebindings command can be used to list the Cluster Role Bindings, which can be used in any project.
~]$ oc get clusterrolebinding
NAME ROLE AGE
my-admins ClusterRole/admin 157s
my-basic-users ClusterRole/basic-user 106s
my-view-only ClusterRole/view 205s
The oc describe rolebinding or oc describe clusterrolebinding command can be used to display the details for a specific Role Binding. If the user, group or service account is not associated with a role binding, this will often cause "User cannot get resource in API group" to be returned.
~]$ oc describe clusterrolebinding my-basic-users
Name: my-basic-users
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: basic-user
Subjects:
Kind Name Namespace
---- ---- ---------
Group my_group
In this scenario, you will either want to create a new Role Binding or Cluster Role Binding and map one or more users / groups / service accounts to the Role Binding
- oc create rolebinding - To create a Role Binding in a specific project and map one or more users / groups / service accounts to the Role Binding
- oc create clusterrolebinding - To create a Cluster Role Binding and map one or more users / groups / service accounts to the Cluster Role Binding
~]$ oc create clusterrolebinding my-view-only --clusterrole view --group my_group
clusterrolebinding.rbac.authorization.k8s.io/my-basic-users created
Or, if there is already a Role Binding or Cluster Role Binding that can be used, you can Map a User Group or Service Account to a Role Binding or Cluster Role Binding.
~]$ oc adm policy add-cluster-role-to-user basic-user john.doe
clusterrole.rbac.authorization.k8s.io/basic-user added: "john.doe"
Notce in these examples that the role binding contains a role, "view" in the first example and "basic-user" in the second example. view and basic-user are roles that grant certain permissions. The oc describe role or oc describe clusterrole command can be used to list the role policy.
~]$ oc describe clusterrole view
Name: view
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods [] [] [get list watch]
Notce this the example at the beginngin of this article that user john.doe is not allowed to list pods in the default namespace. In this example, user john.doe will need to have a role binding that is associated with a role or cluster role that allows "list" on "pods".
Error from server (Forbidden): pods is forbidden: User "john.doe" cannot list resource "pods" in API group "" in the namespace "default"
Also, this blog post and this blog post and this stackoverflow post mention that this may occur if the users hidden .kube folder is not owned by the user. In this example, you would validate that /home/john.doe/.kube is owned by john.doe.
~]$ ls -lisa
7341329 0 drwxr-xr-x. 3 john.doe john.doe 33 Jun 14 03:56 .kube
Did you find this article helpful?
If so, consider buying me a coffee over at 