
If you are not familiar with the oc command, refer to OpenShift - Getting Started with the oc command.
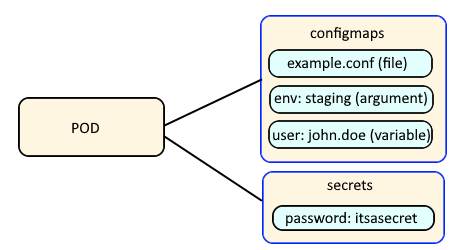
Config Maps are used to:
- mount configuration files in a container
- create environment variables in a container
- create command line option arguments in a container
Secrets are similar, used to create variables that contain encoded data (e.g. passwords). In this way, if a change is needed to a configuration file, variable, or command line option argument, you just need to update the config map or secret as opposed to having to make the change to your applications or deployments.
The following types of secrets can be created. The TLS type of secret will not validate that the key value pairs of the secret conform to a specific structure, whereas the other types of secrets will.
- Opaque (default)
- kubernetes.io/service-account-token. Uses a service account token.
- kubernetes.io/dockercfg. Uses the .dockercfg file for Docker credentials.
- kubernetes.io/dockerconfigjson. Uses the .docker/config.json file for Docker credentials.
- kubernetes.io/basic-auth
- kubernetes.io/ssh-auth
- kubernetes.io/tls
Let's say you used this one liner OpenSSL command to create a self signed public certificate example.cer and private key example.key.
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout example.key -out example.cer -subj "/C=US/ST=California/L=Los Angeles/O=FreeKB/OU=IT/CN=example.com"
The private key file must not be encrypted. If the private key is encrypted, "error: tls: failed to parse private key" will be returned when attempting to create the TLS secret. In the example OpenSSL command above, the -nodes option is used to create an unencrypted private key.
~]$ cat example.key
-----BEGIN ENCRYPTED PRIVATE KEY-----
Here is how you would create a TLS secret.
~]# oc create secret tls my-tls-secret --cert example.cer --key example.key
secret/my-tls-secret created
Or, Let's say you have a YAML file named secret.yml that contains the following markup.
apiVersion: v1
kind: Secret
type: kubernetes.io/tls
metadata:
name: my-tls-secret
namespace: my-project
data:
tls.crt: <data>
tls.key: <data>
The tls.crt data would contain the output from the following command.
cat example.cer | base64 | sed ':label; N; $! b label; s|\n||g'
The tls.key data would contain the output from the following command.
cat example.key | base64 | sed ':label; N; $! b label; s|\n||g'
The oc apply or oc create command with the -f or --filename option can be used to create the secret using the template JSON or YAML file.
The oc replace command can be used to replace a secret using a new or updated template JSON or YAML file.
The oc edit command can be used to update a secret template YAML file.
~]$ oc create --filename secret.yml
secret/my-tls-secret created
The oc get secrets command can be used to list the secrets that have been created.
~]# oc get secrets
NAME TYPE DATA AGE
my-tls-secret kubernetes.io/tls 1 30s
The --output yaml or --output json options can be used to display the YAML or JSON details of the secret.
~]$ oc get secrets my-tls-secret --output yaml
apiVersion: v1
data:
tls.crt: <data>
tls.key: <data>
kind: Secret
metadata:
creationTimestamp: "2021-11-18T07:12:09Z"
name: mysecret
namespace: default
resourceVersion: "448072461"
uid: 4104a646-84e2-46c3-bd59-408e2f7ee807
type: kubernetes.io/tls
You could then configure a deployment to use my-tls-secret. Here is an example of what you could add for the deployment YAML to use the public certificate and private key in my-tls-secret.
AVOID TROUBLE
If there is already a pod running for the deployment, and you update the deployment YAML, you will need to delete the pod so that a new pod gets create, because pods will not detect changes made to the deployment YAML.
spec:
containers:
spec:
volumeMounts:
- mountPath: /etc/pki/tls/private
name: my-certificate
volumes:
- name: my-certificate
secret:
defaultMode: 420
secretName: my-tls-secret
Did you find this article helpful?
If so, consider buying me a coffee over at 