
There are multiple different types of Identity Providers (IdP) that OpenShift can use for authentication.
- htpasswd
- kubeadmin
- LDAP sync (Active Directory)
- Red Hat build of the Keycloak Operator
- Red Hat Single Sign-On (SSO)
Both the Red Hat build of the Keycloak Operator and Red Hat Single Sign-On (SSO) (this article) use keycloak as the backend Identity Provider (IdP) system. Red Hat Single Sign-On (SSO) is much easier to install and configure but may limit you from being able to use or configure certain features. For example, Red Hat Single Sign-On (SSO) installs and configures a Postgres SQL database for you, whereas with Red Hat build of the Keycloak Operator you install and configure the Postgres SQL database.
This assumes you have already:
- Installed the Red Hat Single Sign On (SSO) Operator
- Created the keycloak resource for Red Hat Single Sign On (SSO)
- You can sign into the Red Hat Single Sign On (SSO) console
In the Red Hat Single Sign On (SSO) console, select the Clients tab and select Create.
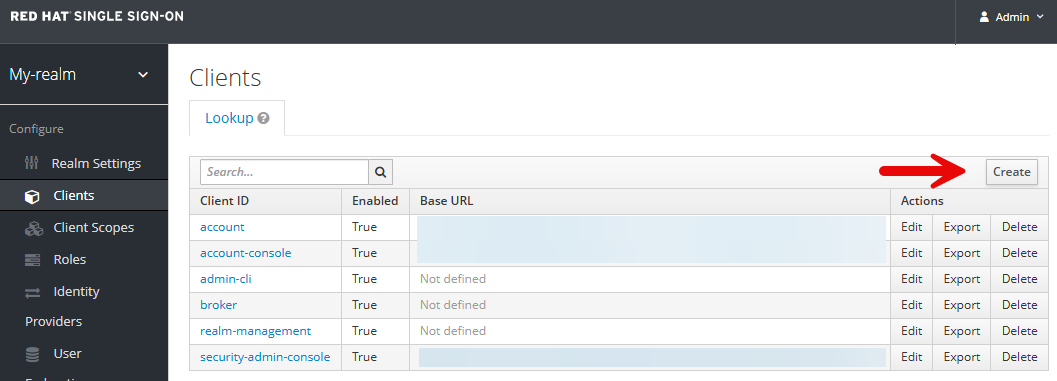
Create an OpenID Connect Client.
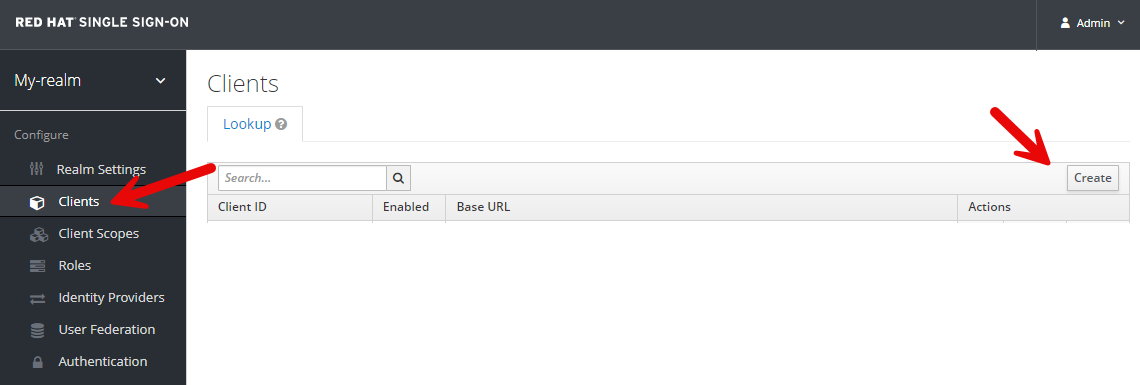
Update the Access Type from public to confidential.
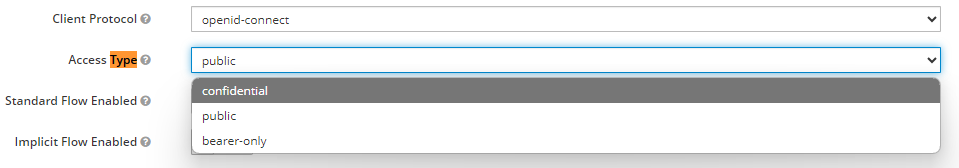
And let's enter our OpenShift console URL in the Valid Redirect URLs.
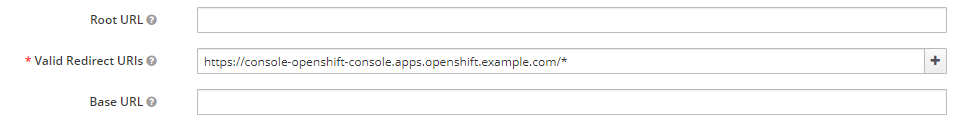
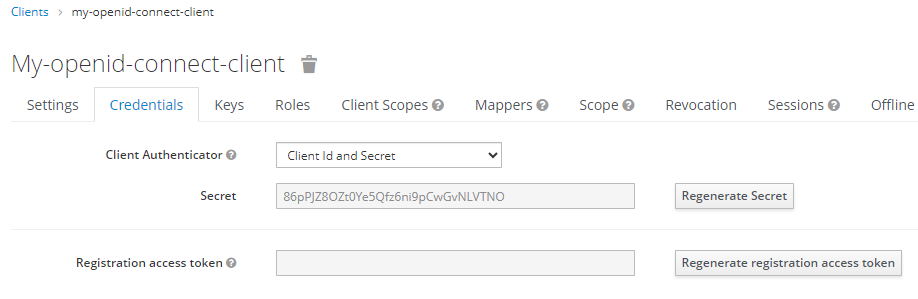
After selecting Save there should now be a Credentials tab with a Secret. Let's make note of the Secret as we'll need this in the next step when updating the OpenShift Identity Provider.
This should create a secret named openid-client-secret-<random string> in the openshift-config namespace.
~]$ oc get secrets --namespace openshift-config
NAME TYPE DATA AGE
openid-client-secret-kqflt Opaque 1 4d
And the secret should contain whatever value you created for the client ID secret.
~]$ oc get secret openid-client-secret-kqflt --namespace openshift-config --output jsonpath="{.data.clientSecret}" | base64 --decode
my-idp-secret
Did you find this article helpful?
If so, consider buying me a coffee over at 