
On a Debian system (Ubuntu, Mint), apt-get install can be used to install OpenSSH server. On a Red Hat distribution (CentOS, Fedora, Red Hat), dnf install or yum install can be used.
dnf install openssh-server
The ps command can be used to determine if your system is using init or systemd. If PID 1 is init, then you will use the service command. If PID 1 is systemd, then you will use the systemctl command.
If your system is using systemd, use the systemctl command to start and enable sshd.
systemctl enable sshd
systemctl start sshd
systemctl status sshd
If your system is using init, use the chkconfig and service commands to start and enable sshd.
chkconfig sshd on
service sshd start
service sshd status
After OpenSSH is active and running, connect using the Linux Terminal or connect using PuTTY. If you are unable to connect to the SSH server, view the SSH logs.
[root@server1 ]# tail /var/log/auth.log
[root@server1 ]# tail /var/log/secure
The last command can be used to confirm that a user is able to make an SSH connection to the OpenSSH server. In this example, john.doe made an SSH connection to the server from client1.example.com. Root did not make an SSH connection to the server, as root connected from server1.example.com, which is the same exact hostname as the OpenSSH server in this example.
[root@server1 ~]# last
john.doe /dev/pts/0 client1.example.com Thu Jan 12 12:04 still logged in
root /dev/tty1 server1.example.com Wed Jan 11 12:54 - 13:13 (00:19)
reboot system boot 3-10-0-327.e17.x Wed Jan 11 12:52 - 13:10 (00:01)
. . .
The /var/log/auth.log or /var/log/secure file will also show SSH connections. In this example, john.doe made an SSH connection to the OpenSSH server.
[root@server1 ~]# tail /var/log/secure
May 6 21:29:10 server1 sshd[15970]: pam_unix(sshd:session): session open for user john.doe by (uid=0)
. . .
May 6 21:51:09 server1 sshd[15970]: pam_unix(sshd:session): session closed for user john.doe
Security
- Configure the /etc/hosts.allow and /etc/hosts.deny files
- Configure iptables.
To ensure the OpenSSH server is secured, view the /var/log/auth.log or /var/log/secure file.
[root@server1 ]#
tail -30 /var/log/auth.log
tail -30 /var/log/secure
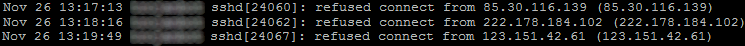
The log typically has attempted connections from foreign IP addresses with a message such as refused connect from foreign ip address.
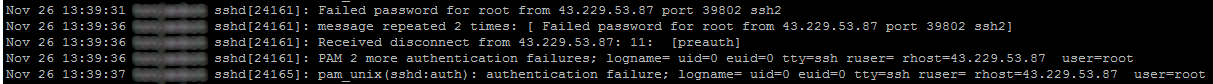
If the log file shows numerous events from a foreign IP address with sshd and message Failed password for root from ip address, this means connections to the OpenSSH server from external hosts is allowed. In this example, an external host is attempting using brute force in an attepmpt to guess the root password to make an SSH connection to our server. In this scenario, the /etc/hosts.allow, /etc/hosts.deny or iptables was not properly configured to refuse SSH connections from foreign hosts.
PKI
By default, OpenSSH is configured to allow connections using the following methods:
- username / password
- public / private key pair (PKI)
For the best security, configure OpenSSH to only allow connections using a public / private key pair.
Did you find this article helpful?
If so, consider buying me a coffee over at 