
There are multiple different types of Identity Providers (IdP) that OpenShift can use for authentication.
- htpasswd
- kubeadmin
- LDAP sync (Active Directory) (this article)
- Red Hat build of the Keycloak Operator
- Red Hat Single Sign-On (SSO)
To import users and groups into OpenShift using LDAP you can create an oAuth LDAP Identity Provider custom resource. The oAuth LDAP Identity Provider will obtain the LDAP bind password to authenticate to your LDAP identity provider from a secret. The oc create secret command can be used to create the secret.
oc create secret generic ldap-secret --from-literal=bindPassword=<your_ldap_bind_password> --namespace openshift-config
Once created, the oc get secret command can be used to verify the secret exists and contains the correct LDAP bind password.
~]$ oc get secret ldap-secret --namespace openshift-config --output yaml
apiVersion: v1
data:
bindPassword: itsasecret
kind: Secret
metadata:
creationTimestamp: "2023-08-16T18:58:06Z"
name: ldap-secret
namespace: openshift-config
resourceVersion: "29051910"
uid: eace4934-9393-48ab-8b05-c75c1575ae77
type: Opaque
The oAuth LDAP Identity Provider will also obtain the Certificate Authority (CA) public certificate that can be used to establish a secured connection to your LDAP identity provider from a config map. The oc create configmap command can be used to create the config map.
oc create configmap ca-config-map --from-file=ca.crt=/path/to/ca.pem --namespace openshift-config
The following YAML is the basic syntax for the oAuth LDAP Identity Provider custom resource. Notice in this example that the bindPassword is stored in a secret named ldap-secret and the Certificate Authority (CA) is stored in a config map named ca-config-map.
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
name: cluster
spec:
identityProviders:
- name: ldapidp
mappingMethod: claim
type: LDAP
ldap:
attributes:
id:
- dn
email:
- mail
name:
- cn
preferredUsername:
- uid
bindDN: ""
bindPassword:
name: ldap-secret
ca:
name: ca-config-map
insecure: false
url: "ldaps://ldaps.example.com/ou=users,dc=acme,dc=com?uid"
The oc apply command can be used to apply the oAuth YAML file to create the oAuth custom resource.
oc apply -f oauth.yml
Or in the OpenShift console, at Administration > CustomResourceDefinitions > Create CustomResourceDefinition, the oAuth custom resource (CR) can be created.
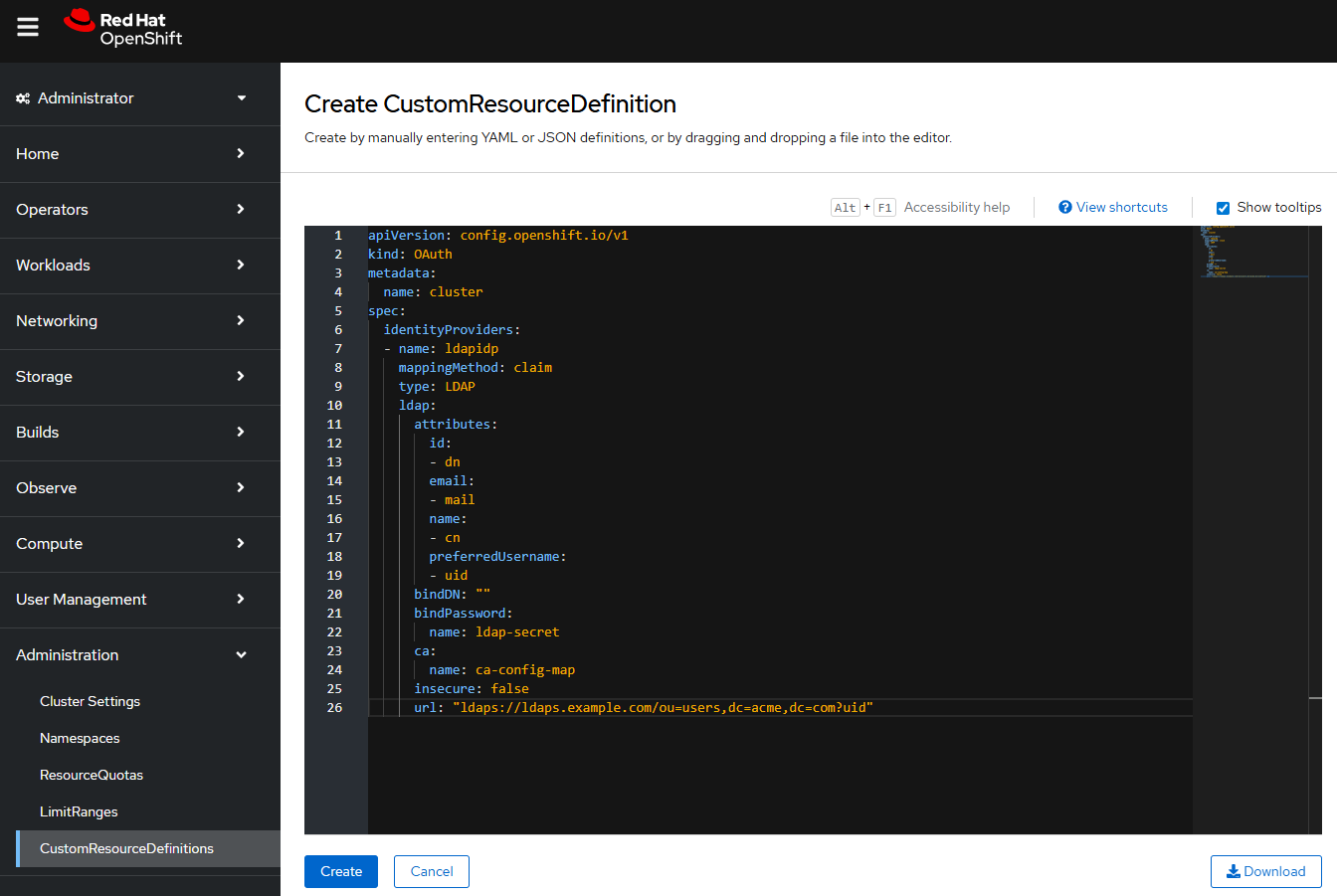
Once created, there should then be an oAuth resource.
~]$ oc get oauth
NAME AGE
cluster 3y304d
And the oc get oauth command with the --output yaml or json option can be used to see the YAML or JSON.
~]$ oc get oauth cluster --output yaml
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
creationTimestamp: "2020-09-30T15:41:25Z"
name: cluster
resourceVersion: "1730679458"
uid: f1a37a7e-17ce-4747-8c53-171fa3f767bc
spec:
identityProviders:
- ldap:
attributes:
email:
- mail
id:
- dn
name:
- cn
preferredUsername:
- uid
bindDN: ""
bindPassword:
name: ldap-ad-secret
ca:
name: ca-config-map
insecure: false
url: ldaps://ldaps.example.com/ou=users,dc=acme,dc=com?uid
mappingMethod: claim
type: LDAP
An LDAP entry typically has a format like this. In this example, Common Uame (cn) john.doe is in the People Organizational Unit (ou) in the example.com Domain Controller (dc).
cn=john.doe,ou=People,dc=example,dc=com
In this example, User ID (uid) john.doe is in the People Organizational Unit (ou) in the example.com Domain Controller (dc).
uid=john.doe,ou=People,dc=example,dc=com
Notice that the oAuth Identity Provider custom resource has mappingMethod:claim and preferredUsername:uid. This means that the oAuth Identity Provider will look for a User ID (uid) entry in LDAP.
Assuming the LDAP entry is uid=john.doe, John Doe should be able to log into OpenShift.
oc login -u john.doe
If john.doe is able to log into OpenShift, two resources should be created, the User resource and Identity resource.
The oc get users command can be used to list the users that have logged into OpenShift.
IMPORTANT
Users will not be listed until they have logged into OpenShift at least once.
~]# oc get users
NAME UID FULL NAME IDENTITIES
jane.doe 6b9b184a-cfea-44bf-ad62-a4a3454881cc jane.doe htpasswd_provider:jane.doe
john.doe 5ad8f659-64ce-4c9c-9ca0-fe69521fd7f2 john.doe my-ldap:Y249YzA0NDIwNixvdT11c2VycyxPPVRocml2ZW50
Similarly, the oc list identities command can be used to list the users that exist on the system under a particular identity provider.
IMPORTANT
Identities will not be listed until they have logged into OpenShift at least once.
~]$ oc get identity
NAME IDP NAME IDP USER NAME USER NAME USER UID
my-ldap:Y249YzA0NDIwNixvdT11c2VycyxPPVRocml2ZW50 my-ldap Y249YzA0NDIwNixvdT11c2VycyxPPVRocml2ZW50 john.doe 5ad8f659-64ce-4c9c-9ca0-fe69521fd7f2
Did you find this article helpful?
If so, consider buying me a coffee over at 